Users
Core functionality of Loft is giving other people self-service access to Kubernetes clusters. Everyone who should get access to a Kubernetes cluster, must be an authenticated user in Loft.
Working with Users
Create User (manual)
Loft lets you connect a variety of SSO providers for authentication but you can also manually create users who can sign in via username and password:
Create a User
- Go to the Users view using the main menu on the left
- Click on the button
- Use the field Display Name to enter the Username for your user
- Click on the button at the very bottom
- Close the popup using the button
Impersonate User
Loft allows admins with appropriate RBAC permissions to impersonate users.
Impersonate User
- In the Users view, hover over the row with the User who you want to impersonate
- While hovering over the row, you will see buttons appear on the right in the Actions column
- Click on the button to Impersonate the user
- In the popup, click on the button to confirm that you want to start impersonation
- Whenver you want to switch back to your regular user, click the button on the right-hand side of the impersonation banner at the top of the page
To use Loft CLI as the impersonated user, you can run the following command while impersonation is active:
loft login localhost:9898 --insecure # or use your loft.domain.tld instead of localhost, and ideally with a valid SSL cert and without the --insecure flag
You can verify the login and print your user information via:
loft login
Configuration
Metadata
Display Name
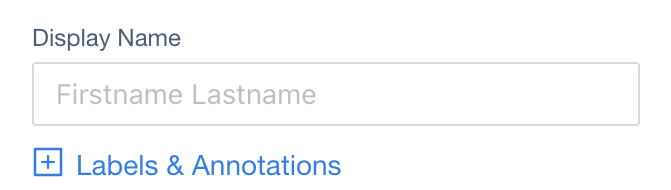
JSONPath in User CRD:
spec.displayName (type: string)
Kubernetes Name
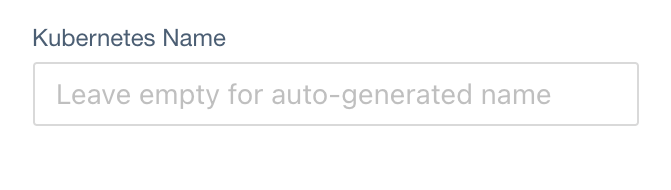
JSONPath in User CRD:
metadata.name (type: string)
Labels

JSONPath in User CRD:
metadata.labels (type: map[string]string)
Annotations

JSONPath in User CRD:
metadata.annotations (type: map[string]string)
User Information
Username
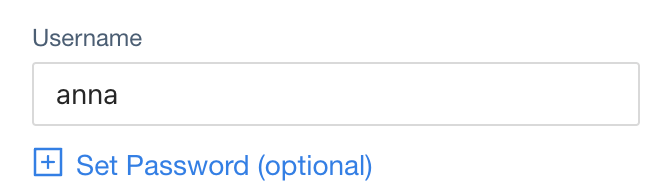
JSONPath in User CRD:
spec.username (type: string)
Email

JSONPath in User CRD:
spec.email (type: string)
Password
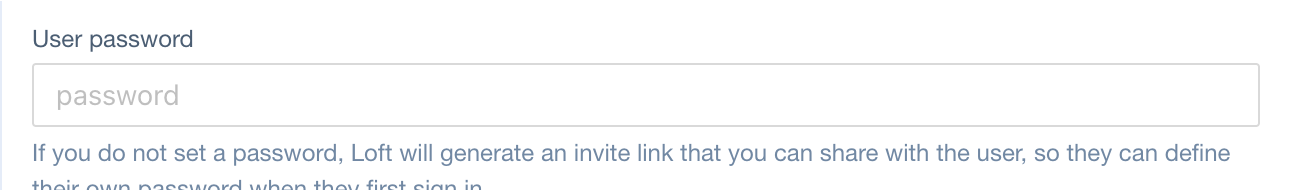
JSONPath in User CRD:
spec.passwordRef (type: SecretRef)
Team Memberships

JSONPath in Team CRD:
$team.spec.users (type: string[])
Advanced Options
Kubernetes Groups
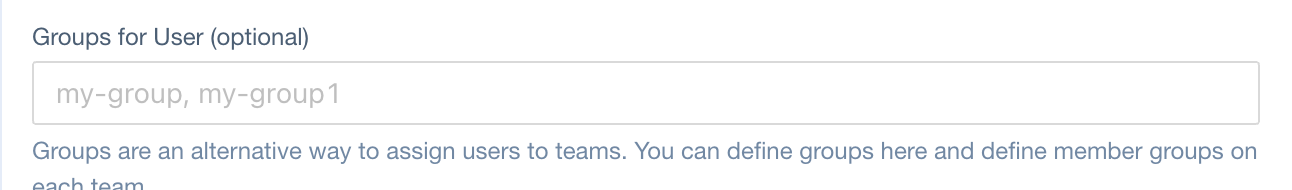
JSONPath in User CRD:
spec.groups (type: string[])
Cluster Roles
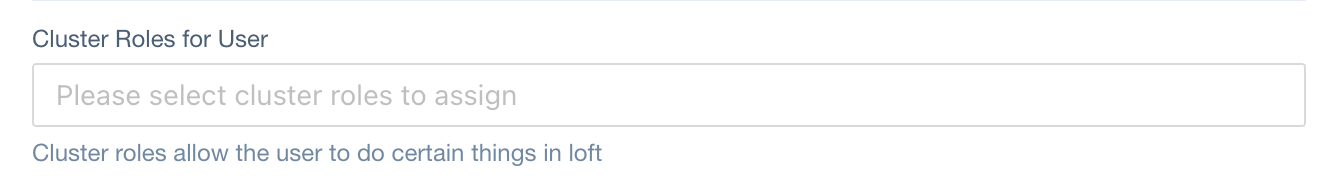
JSONPath in User CRD:
spec.clusterRoles (type: ClusterRoleRef[])
Image Pull Secrets
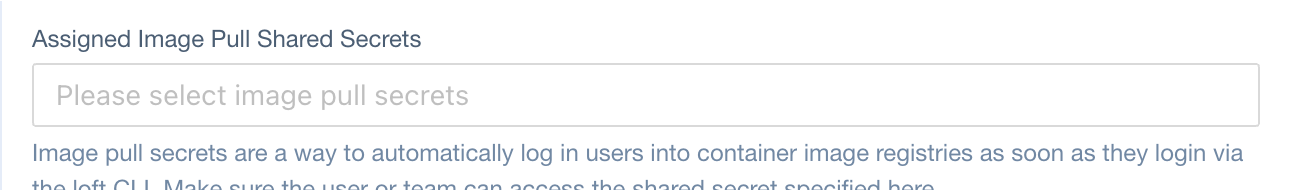
JSONPath in User CRD:
spec.imagePullSecrets (type: SecretRef[])
Access To User
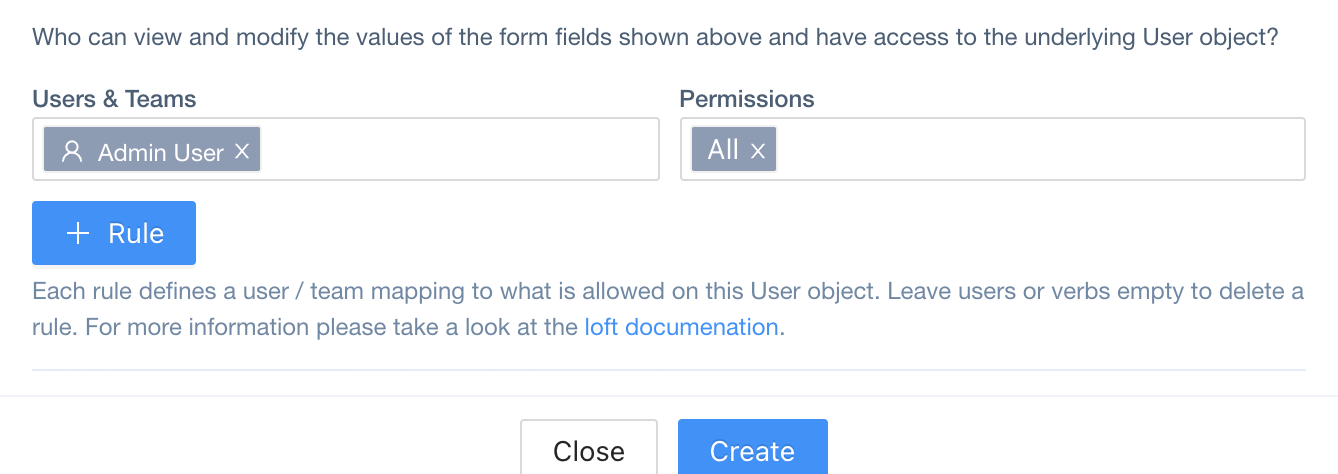
JSONPath in User CRD:
spec.access (type: Access[])